Google is a highly successful internet business. Recently they have broaden their scope with multitude new tool. Research Google business model and answer the following questions below. You may add additional information not included in this question.
1. Who are their competitors?
We face competition in every aspect of our rapidly evolving business, particularly from other companies that seek to connect people with online information and provide them with relevant advertising. Currently we consider our primary competitors to be Microsoft and Yahoo.
A year ago, Google named just two competitors -- Microsoft and Yahoo -- in its annual report to the U.S. Securities and Exchange Commission. This year, Google lists 10 competitors by name in its recently filed 10-K report for 2009, including social sites Facebook, Twitter, and Yelp; and specialty search engines that dive deep into a specific category, such as travel site Kayak and health inquiry site WebMD.
With the explosive growth of social networks acting as the door to people's online world, Google does face increased competition. But with the Mountain View, Calif.-based search giant facing a surge of antitrust and anticompetition lawsuits and allegations in the U.S. and Europe, observers and critics say the change shows Google's pressing need to make the case to regulators that it has viable competitors, and has not become too dominant an Internet force.
"There aren't a flood of new companies that have entered the market that are suddenly Google competitors that weren't there last year, but they are calling them out in a more direct way," said Greg Sterling, principal of Sterling Market Intelligence, adding that if regulators see Google as a company without legitimate competition, "that perception is a big problem for them politically."
Nevertheless, he said the rapid growth of Facebook and Twitter during 2009, and the effectiveness of specialty search engines like job site Monster.com, show that Google's "competition is broader than simply Yahoo and (Microsoft's search engine) Bing."
For its part, Google in its SEC filing calls the increasing power of specialty, or "vertical" search engines like Kayak, which allow people to root through scores of airlines for the cheapest flights, and the emergence of mobile applications on platforms like the
iPhone that allow consumers to directly access a Web product without going through a search engine, "formidable" competition.
2. How have they use information technology to their advantage?
Cloud computing is in Google's DNA Google has been pushing the technological bounds of cloud computing for more than ten years. Today, feedback and usage statistics from hundreds of millions of users in the real world help us bring stress-tested
... Expand innovation to business customers at an unprecedented pace. From our consumer user base, we quickly learn which new features would be useful in the business context, refine those features, and make them available to Google Apps customers with minimal delay. Collapse
Faster access to innovation drives higher productivity The web is the epicenter of innovation, and Google's multi-tenant infrastructure is designed so we can push improvements to our entire customer base on short iteration cycles. We can deliver new functionality
... Expand on a weekly basis, or faster, because our systems are able to distribute updates so efficiently. In 2009 alone, we launched over 100 improvements, and customers didn't need to manage any upgrades or patches. In contrast, businesses tend to update traditional server software every five to seven years due to long release cycles from vendors and the cost and complexity businesses face implementing upgrades, especially when more powerful servers are required, like 64-bit hardware.
Browser-based applications are another key ingredient in our recipe for rapid innovation. When we launch new features in our web applications, users automatically get these improvements just by refreshing their browsers. Our mobile browser applications also get new features without software updates. With traditional technology and "software plus services", client software is an innovation bottleneck. Even after back-end systems can support new features, users don't get new functionality in those environments until the software on their computers and mobile phones have been upgraded, which can be an expensive and labor-intensive project. Collapse
3. How competitive are they in the market? Google Analytics has now been around for some time. Google Analytics is a free web application that helps web masters learn everything they want to know about how their visitors found their site and how they interact with their site. They are able to focus on their marketing resources on campaigns and initiatives that deliver ROI, and improve their site to convert more visitors.
But what can Google get in return: Competitive Market Research regarding the Search marketplace.
Using Google Analytics Aggregated data Google can collect statistics regarding other search engines and how they refer you to sites.
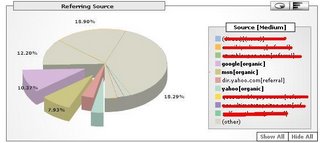
In effect what keywords they refer, vs. what keywords others refer. They also can get raw counts in the number of unique visitors and total visitors by referrer
This is only possible because Google Analytics is a centralized web application maintained and operated by Google vs.
AWStats another common used alalytics platform which is installed maintained and operated by the webmaster.
4. What new services do they offer?- Google Lively was a web-based virtual environment that allowed as many as 20 people to sit in a virtual room and chat with each other. The offering debuted in July 2008 only to have Google pull the plug a mere four months later.
- Google Print Ads was dropped earlier this year after the company’s vision of bringing web-like automation to the world of traditional media failed to materialize. The effort went belly-up just three weeks before the death of Google Audio Ads, which ended a three-year run in February after the company failed to gain traction in the radio ad game.
- Google Answers spent a year in beta before a full-blown launch in May 2003, but the effort to create a fee-based knowledge market never gained much traction outside a small base of users and the service was dropped in late 2006.
- The social networking site Orkut launched early in 2004 as an independent project of noted Google developer Orkut Büyükkökten and has caught fire in Brazil, a market that accounts for roughly 50 percent of its membership. The site reportedly claims roughly 100 million users, which is impressive, but Google can’t be happy that its effort is virtually unknown in Europe and North America while Facebook, LinkedIn, MySpace and others have gained such impressive traction.
- Google Catalog Search debuted in 2001 as a way for consumers to go online to check out their favorite print catalogs that had been scanned and uploaded. Of course, retailers were already taking their inventories online themselves, and the effort was put to rest earlier this year.
- Google Health was released as a beta test in May 2008, but the service has yet to find much of an audience among insurers or the general public. Which may have something to do with the combination of the words “health” and “beta test.”
- The location-based service Dodgeball was shut down in 2009 after Google had acquired it four years earlier, and while Google continues to operate Jaiku – a social networking service it picked up in 2007 — the company has effectively abandoned the project. The technologies and expertise from both startups is being incorporated into other Google businesses and projects, however.
5. What them so unique? Previously I’ve written about the
corporate culture at Google and how it isn’t likely to be an easy thing to emulate. Today at work, my coworker,
Jackson, showed me
this post that links to a slide show that delves into Google’s internal processes. Another post that I recently read was
Steve Yegge’s post on Good Agile, Bad Agile, in which Steve explores Google’s version of agile.
Needless to say, it all adds up to a lot of Google on the brain. Google, at the moment, is held up as the gold standard of software companies. They have achieved massive success and are the company almost every developer wants to work for. Ask someone in the software industry which company they want to emulate and they will likely say Google.
Obviously, if it was easy to emulate Google, everyone would have done it or would be doing it by now. The more I think about Google, the more and more I think it is going to be impossible to emulate them. Certainly you can steal some of their ideas and what they’ve pioneered and put it to use in your company, but outright copying Google is going to be near impossible.
Having touched on Google’s corporate culture, let’s look at something else that makes Google even more unique: how it grows.
One thing that has become evident to me is that Google grows in an organic fashion, unlike any other company I know of. Google develops tools that are internally useful and then releases them to the world. Google does not develop products to sell to the world. Google does not have external contracts, at least in the traditional sense, as far as I can tell.
Let me elaborate on this. Google is obviously best known for search and for ads associated with search. This is in essence Google’s one true product. It is the one feature Google developed for the outside world. When Google developed search it was no different from a small company. It is what Google has done since then that makes Google different.
6. How competitive are they in the international market?
Having studied Google abroad somewhat significantly, I believe this article provides a very naïve view on Google’s success abroad. Absolutely, Google, as any American company, needs to be extremely aware of the impression they make when entering foreign grounds, as the risk as being seen as arrogant – the ugly American – is omnipresent. And, yes, Google should continue to grow their in-country teams significantly in order to best overcome cultural and sales hurdles and take advantage of unique opportunities and the gigantic world market that is growing at a quicker pace than the U.S. market. Recent stats point to European e-commerce in a position to surge past U.S. e-commerce.
Yet, don’t attempt to fool anyone here: Google has enormous international market share. Though I’m on a plane and not able to access these stats immediately, I believe that Google has approximately a 10-point higher share of search in Europe than they do in the States. I attended an online and multi-channel retail conference in London earlier this year, and Google was constantly mentioned, and never in a bad light. I am attempting to arrange a dinner in Paris later this year or early next with top French e-commerce companies, and Google is the likely sponsor, due to their relationship with the French agency that I am in contact with and their relationship with the likely invitees. Google is dominant in most countries, with their distant following to Baidu in China and the Russian example in the article notable exceptions.
In the UK, Amazon.com and eBay have also taken off after some early slips and command a dominant share of the market. Of course, they face hurdles, most notably eBay’s fraud and trust problem, but these American brands have also experienced tremendous success abroad. And there are other huge hurdles across Europe, such as Germany’s reliance on non-credit card payments and their language and cultural barriers. The European Union is still quite segmented, and pan-European plays will rarely be successful. Yet, the world continues to flatten, and American brands can have success abroad with fewer hurdles as can international brands have success in the States.
Google has had success with other products abroad, most notably its Orkut social network which has bombed domestically to its MySpace, Facebook, and LinkedIn brethren, yet has taken off in huge countries such as India and Brazil. So, sure, Google should be sensitive to cultural sensitivities and will face different regulatory environments abroad, but the truth is that Google has been remarkably successful internationally in large part due to the international word-of-mouth generated by their product and feature set.



